Similar to 信頼できるコンピューティングのセキュリティ開発ライフサイクル
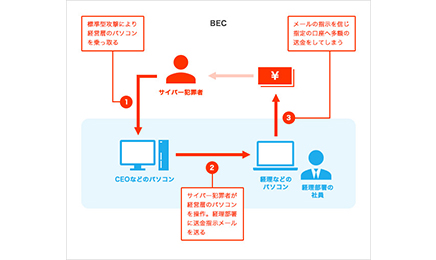
キルチェーン
Kill chain (military)
次世代セキュアコンピューティングベース
Next-Generation Secure Computing Base
セキュリティチェック

本人認証
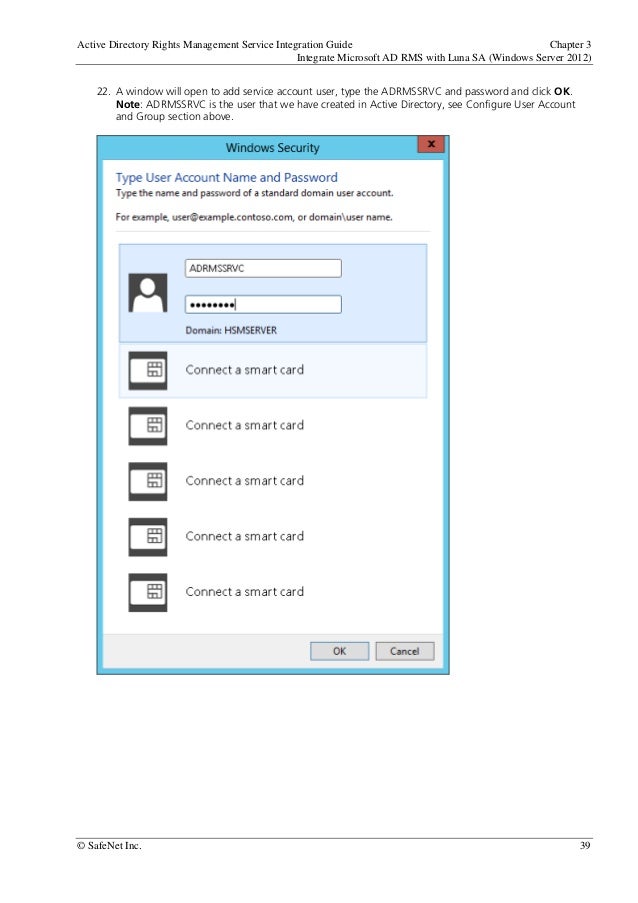
Active Directory Rights Management Services
Active Directory Rights Management Services
Advanced Message Queuing Protocol
Advanced Message Queuing Protocol
AMD Accelerated Parallel Processing
AMD APP SDK
Bare Knuckle Fighting Championship
Bare Knuckle Fighting ChampionshipBerkeley Open Infrastructure for Network Computing
Berkeley Open Infrastructure for Network Computing
Free Software Foundation Latin America
Free Software Foundation Latin America
International Journal of Transgender Health
International Journal of Transgender Health
Internet Speculative Fiction Database
Internet Speculative Fiction Database
Interuniversity Microelectronics Centre
IMEC
Japanese Journal of Clinical Oncology
Japanese Journal of Clinical Oncology
Notices of the American Mathematical Society
Notices of the American Mathematical Society
Security Content Automation Protocol
Security Content Automation Protocol
Security Support Provider Interface
Security Support Provider Interface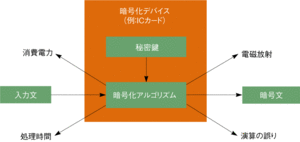
サイドチャネル攻撃
Side-channel attack
総当たり攻撃
Brute-force attack
タイミング攻撃
Timing attack
否認不可
Non-repudiation
アクティブディフェンス
Active defense
サイバースパイ
Cyber espionage
サイバー戦争
Cyberwarfare
AdBlock
AdBlock
Alien (ソフトウェア)
Alien (file converter)
Android 15
Android 15
ANTLR
ANTLR