[新品未開封|SIMフリー] iPhone 16 128GB 256GB 512GB 各色 スマホ 本体view page
amosnier/sha-2Name already in usesha-2
view page
What is the Difference Between SHA1 and SHA256
view page
【中古】iPhone 14 128GB 256GB 512GB A2881 スマホ スマートフォン 本体 SIMフリー ミッドナイト (PRODUCT)RED スターライト パープル ブルー…view page
BACs SHA-2 – don’t make your payroll a dogs dinner
view page
【国内版SIMフリー・新品未開封/未使用品】 iPhone16 128GB 256GB 512GB 各色 スマホ 本体view page
¿Qué es el SHA-2 y en qué nos afecta la inminente transición desde SHA-1?
view page
【中古】iPhone SE 第3世代 2022 SE3 A2782 64GB 128GB スマホ スマートフォン SE3 本体 SIMフリー ミッドナイト レッド スターライト docomo au…view page
Generate SHA1 Hash from Multiple Files in Folder
view page
Resultado de imagen para sha 256 algorithm
view page
【19日20時からポイントUP! 大感謝祭】新品未開封品【Nランク】SIMフリー iPhone17 Pro 256GB Apple シルバー MG854J/A コズミックオレンジ MG864J/A…view page
Part 5: Hashing with SHA-256Step by step hashing with SHA-256
view page
differences_between_sha256_and_scrypt
view page
iPhone 16e simフリー 端末本体のみ (機種変更はこちら) 新品 純正 Apple 認定店 楽天モバイル公式 アイフォン 【ご注文から30分経過後はキャンセル不可】【自宅受け取り限定…view page
【19日20時からポイントUP! 大感謝祭】新品未開封品【Nランク】SIMフリー iPhone16e 128GB Apple A3409 ブラック ホワイト MD1Q4J/A MD1R4J/A…view page
How SHA (Secure Hash Algorithm) works?| Characteristics of SHA| Types of SHASHA - 0SHA -1SHA -256| Conclusions
view page
Les mathématiques de Bitcoin : SHA-256
view page
How we created the first SHA-1 collision and what it means for hash security
view page
純正バッテリー100%|90%【中古】iPhone 15 128GB 256GB 512GB A3089 スマホ スマートフォン 本体 SIMフリー ピンク イエロー グリーン ブルー ブラック…view page
MD5 vs SHA-1 vs SHA-2 - Which is the Most Secure Encryption Hash and How to Check ThemWhat's a hash function?Common hash functionsUsing Hash Values for Validation
view page
The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
view page
How to Migrate Your Certification Authority Hashing Algorithm From SHA-1 To SHA-2Migrating your Certification Authority Hashing Algorithm from SHA-1 to SHA-2SHA-1 is broken, time to migrate to SHA-2Cryptographic providersMigrate your certification authority from CSP to KSPReferences
view page
iPhone 15 simフリー 端末本体のみ (機種変更はこちら) 新品 純正 Apple 認定店 楽天モバイル公式 アイフォンview page
iPhone 17 Pro Max 端末本体のみ(機種変更はこちら) SIMフリー 新品 純正 Apple 認定店 楽天モバイル公式 アイフォン…view page
The SHA-1 Attack Further Emphasizes the Need for Crypto-Agility
view page
SHA-3 vs the world SHA-3 vs the world
view page
SHA-3 vs the world SHA-3 vs the world
view page
【19日20時からポイントUP! 大感謝祭】新品未開封品【Nランク】SIMフリー iPhone17 256GB ブラック MG674J/A ホワイト MG684J/A ミストブルー…view page
Secure Hash Algorithm Secure Hash Algorithm
view page
Back to Basics: Secure Hash Algorithms
view page
New SHA-3 hashing IP from Barco Silex helps customers implement future-proof security
view page
【中古】iPhone SE 第2世代 2020 SE2 A2296 64GB 128GB 256GB スマホ スマートフォン SE2 本体 SIMフリー ブラック レッド ホワイト docomo…view page
純正バッテリー100%|90%【中古】iPhone 14 Pro Max 128GB 256GB 512GB 1TB スマホ スマートフォン 本体 SIMフリー ブラック ゴールド シルバー…view page
SHA-1 algorithm officially dead, Secure Chat not compromised
view page


![[新品未開封|SIMフリー] iPhone 16 128GB 256GB 512GB 各色 スマホ 本体](https://thumbnail.image.rakuten.co.jp/@0_mall/icockaden/cabinet/10962912/11261694/iphone16-all.jpg?_ex=300x300)













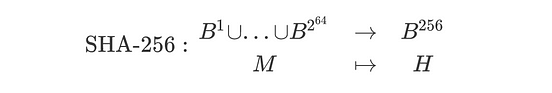


















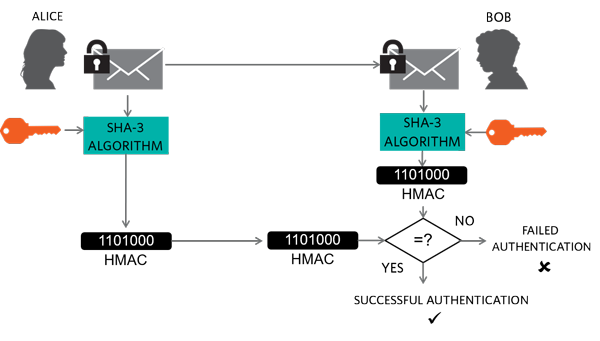



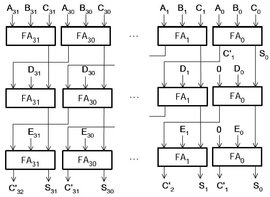





![[字幕動画]Bitcoinの基礎「暗号学的ハッシュ関数」を学ぶ](https://dnaimg.com/2014/03/11/bitcoin-cryptographic-hash-function-fsk/title.jpg)


