SHA-3 vs the world SHA-3 vs the world
view page
【max25%OFFクーポンで825円】 日本製 ヘアドライタオル 綿100% ハービー Halfbe 楽天1位 / シルクプロテイン ドライヤー時間半分 【オギャ子さん×ヒオリエ…view page
SHA-3 vs the world SHA-3 vs the world
view page
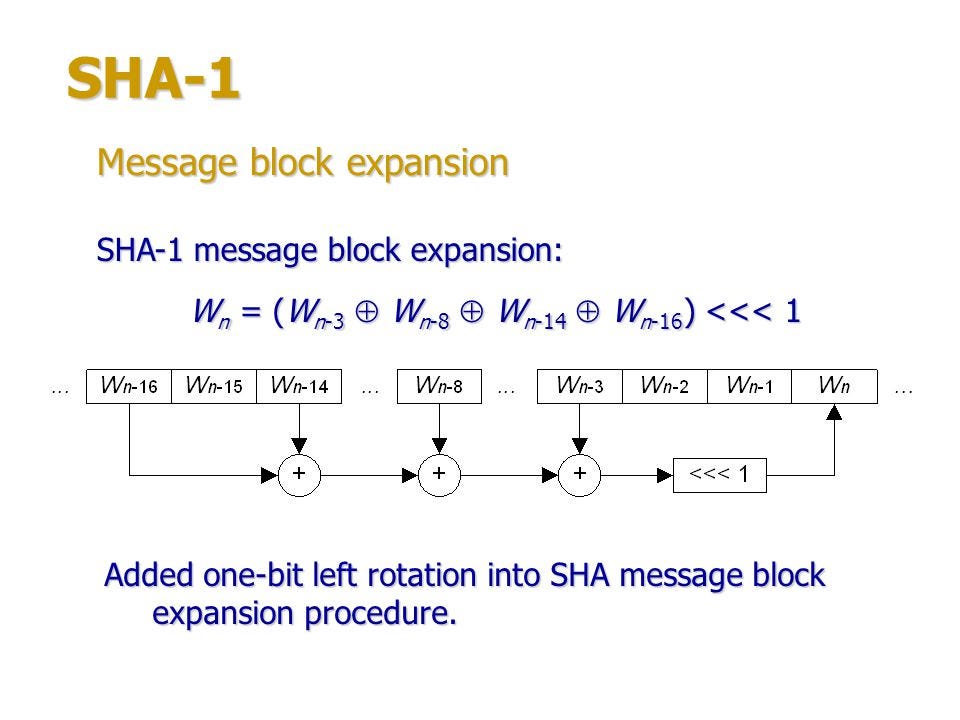
Secure Hash Algorithm Secure Hash Algorithm
view page
Back to Basics: Secure Hash Algorithms
view page
[美容をトータルサポート♪]ナウフーズ ビオチン サプリメント 10mg (10000mcg) 120粒 NOW Foods Biotin ベジカプセル 120日分 ビタミンB群 スキンケア…view page
New SHA-3 hashing IP from Barco Silex helps customers implement future-proof security
view page
SHA-3 Explained in Plain EnglishBackgroundSponge Construction PaddingThe Keccak Function
view page
【楽天1位/レビュー1.3万件★4.64】ヘアブラシ Lefina 豚毛×天然木 高級パドルブラシ ヘッドスパニスト監修 頭皮ケア 頭皮マッサージ 静電気防止 髪質サポート 艶髪 乾燥対策 ギフト…view page
KMAC Slide from the SHA-3 discussion
view page
【送料無料】YASAI シャンプー750ml or ヘアパック600g 大容量タイプ(専用読本付き)通常よりも3倍容量でお得なサイズココナッツ由来最高級洗浄成分配合TAMA Yasai…view page
SHA-3(Secure Hash Algorithm-3)过程简述SHA-3(Secure Hash Algorithm-3)过程简述
view page
Trailer of season 3 of the Award winning series - A.I.SHA 3
view page
【店内P最大56倍以上開催】14種類の豊富な成分により内側から環境をサポート【DHC直販】 ボリュームトップ30日分 | dhc サプリメント サプリ ボリュームトップ ヘアケア 髪…view page
Cryptocurrency Ethereum Classic can change mining algorithm from Ethash to SHA-3 (Keccak 256)
view page
SHA SHA Announces Departure Of 3 Members + Comeback With New Members
view page
【ふるさと納税】髪 すきバサミ 美容師 子供 散髪 貝印 セルフ 痛くない はさみ 【 関孫六 スキハサミ 】ヘアカット ハサミ 鋏 髪切 セルフカット 理美容 家庭用 美容院 髪切りはさみ…view page
The Ethereum Classic SHA 3 Coalition and Migration With Alex Tsankov
view page
【公式】タングルティーザー ザ・アルティメットディタングラー ヘアブラシ 正規品view page
อัลกอริทึม HASH คืออะไรความปลอดภัยการใช้งานและการทำงาน
view page
Project 12x: SHA-3 on Kali Linux (15 pts.)
view page
【UCHINO公式店】ウチノ とってもよく吸う「ごくふわ」 ヘアータオル|内野 タオル 綿100% コットン 抗菌 防臭 吸水 速乾 軽い やわらか ふわふわ 小さめ ヘアタオル ヘアキャップ…view page
Hashing Algorithms: SHA-512 and SHA-3
view page
【最大2000円OFFクーポン配布中】【高濃度 スーパーミレットエキス】お徳用 90粒 約3ヶ月分 ミレットエキス シスチン コラーゲン 亜鉛酵母 髪の毛 ギフト 贈り物 サプリメント ボリューム…view page
Secure Hash Algorithm-3: How SHA-3 is a next-gen security tool
view page
Resultado de imagen para sha 256 algorithm
view page
【店内P最大56倍以上開催】【DHC直販】 美HATSUGA 30日分 | DHC サプリメント サプリ 健康食品 ケラチン 美容 ヘアケア 1ヶ月分 スカルプ スカルプケア 髪 ビタミンサプリ…view page
Part 5: Hashing with SHA-256Step by step hashing with SHA-256
view page
differences_between_sha256_and_scrypt
view page
トリートメントの素 ・100mL 髪の NMF 原料混合液 ケラチン 配合 トリートメントのもと 送料無料view page
髪の毛ポイ捨てシール 浴室排水口用 大サイズ(直径15cm) 10枚入 (100円ショップ 100円均一 100均一 100均)view page
How SHA (Secure Hash Algorithm) works?| Characteristics of SHA| Types of SHASHA - 0SHA -1SHA -256| Conclusions
view page
Les mathématiques de Bitcoin : SHA-256
view page
How we created the first SHA-1 collision and what it means for hash security
view page
髪飾り 美和花 成人式 卒業式 12点セット つまみ細工 セット 3colors 振袖 花 和装 着物 赤 白 黒 ベージュ 袴 かんざし ヘアアクセサリー 上品 レディースview page
MD5 vs SHA-1 vs SHA-2 - Which is the Most Secure Encryption Hash and How to Check ThemWhat's a hash function?Common hash functionsUsing Hash Values for Validation
view page
The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
view page