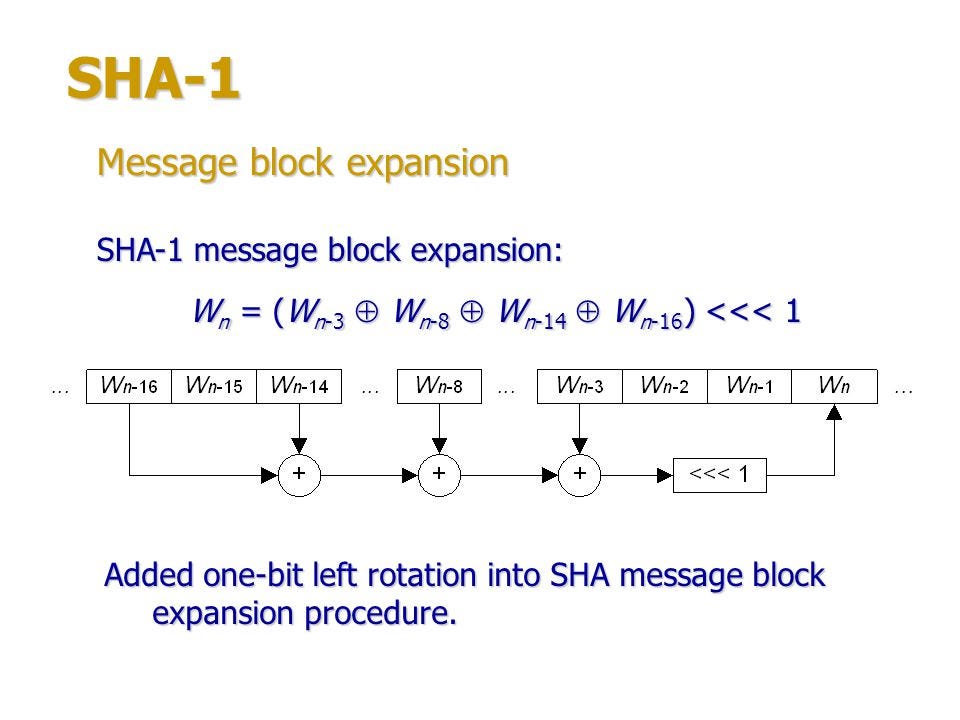
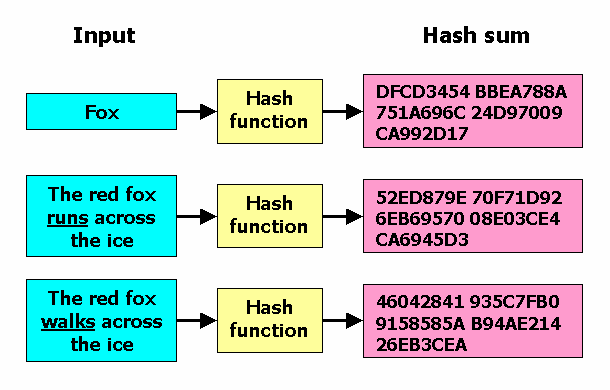
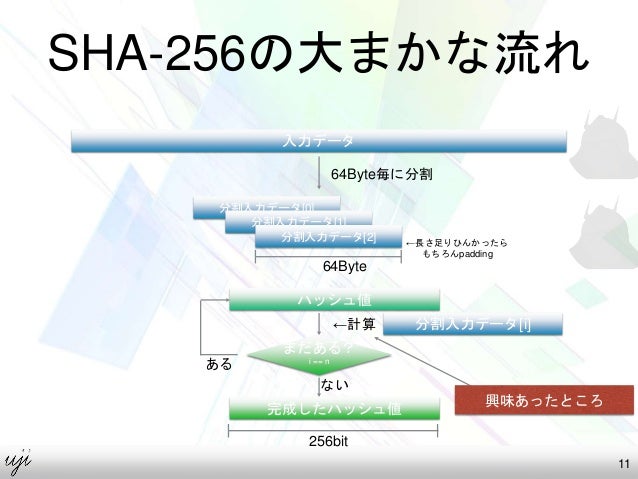
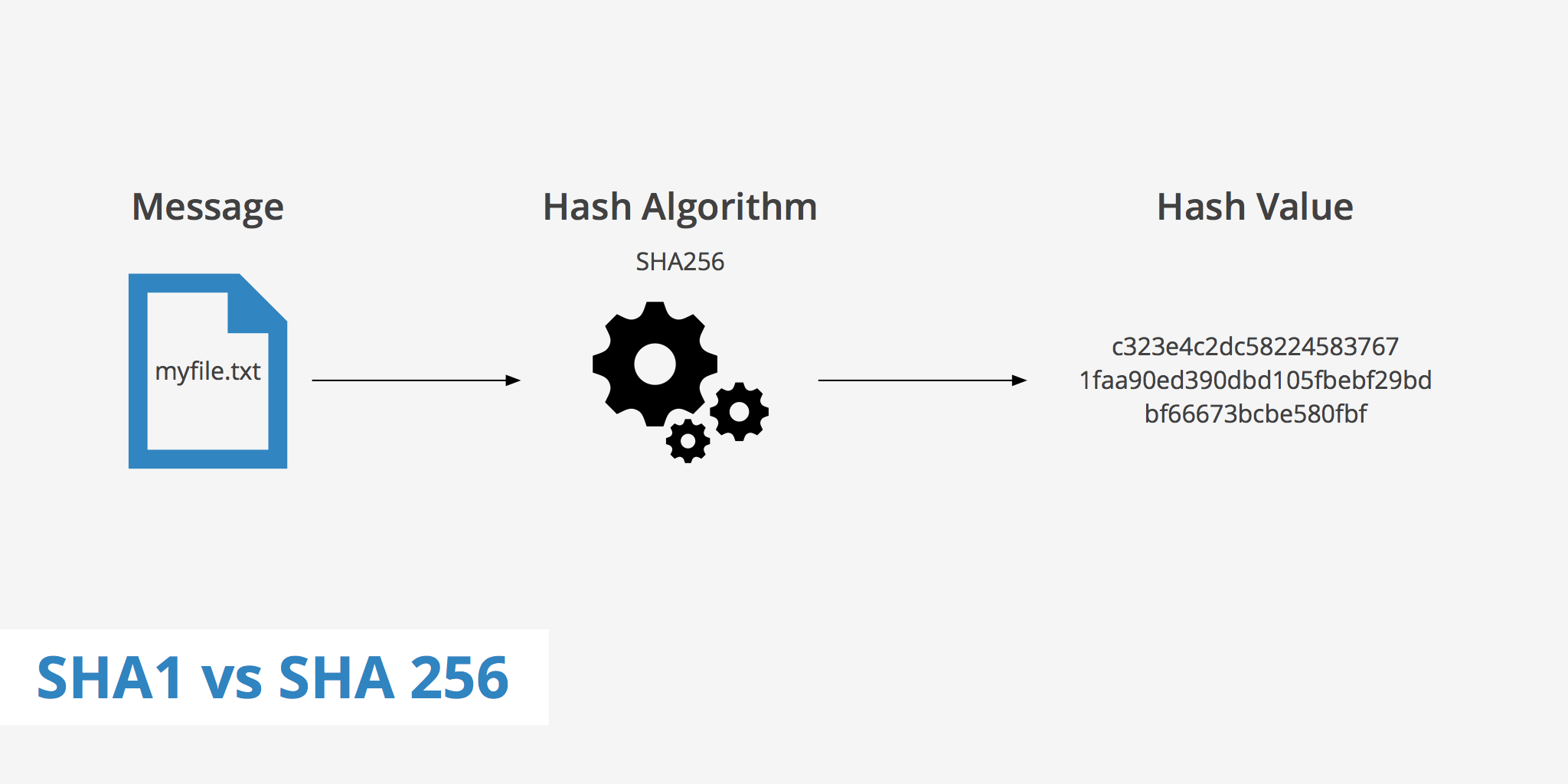
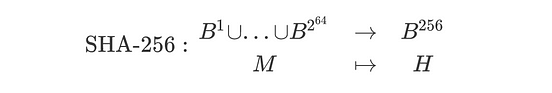Resultado de imagen para sha 256 algorithm
view page
【クーポン&ポイント10倍】お歳暮 冬ギフト プレゼント ギフト クリスマス 2025 百貨店で人気 お菓子 【パティスリーキハチ 公式】 人気 おしゃれ 高級 ギフト ランキング 洋菓子 内祝い…view page
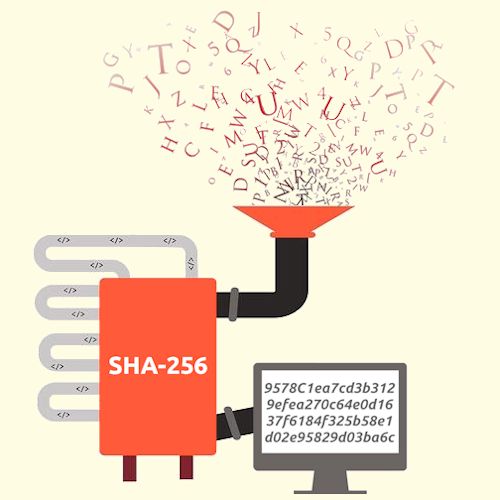
Part 5: Hashing with SHA-256Step by step hashing with SHA-256
view page
【大感謝祭限定★30,000円OFFクーポン!】 電動自転車 a01 折りたたみ 電動アシスト自転車 erway 自転車 電気自転車 パワフル 5段階アシスト搭載 20インチ 7段変速 おしゃれ…view page
differences_between_sha256_and_scrypt
view page
【無料★特典付】 【特別価格】水受けセット ユニソン スプレスタンド60ソリッド 蛇口1個セット+ステンレスパン 蛇口付き立水栓 水栓柱&ガーデンパン 組合せセット 4カラー 1口水栓柱…view page
How SHA (Secure Hash Algorithm) works?| Characteristics of SHA| Types of SHASHA - 0SHA -1SHA -256| Conclusions
view page
Les mathématiques de Bitcoin : SHA-256
view page
【LINE追加で最大2000円OFF】 ガスコンロ リンナイ ガステーブル パールクリスタル ホワイト 白 59cm 両面焼きグリル プロパン 都市ガス 据置型ガスコンロ 2口…view page
How we created the first SHA-1 collision and what it means for hash security
view page
MD5 vs SHA-1 vs SHA-2 - Which is the Most Secure Encryption Hash and How to Check ThemWhat's a hash function?Common hash functionsUsing Hash Values for Validation
view page
The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
view page
【大感謝祭限定★40,000円OFFクーポン+P8倍!】 サスペンション搭載 型式認定済 電動自転車 免許不要 130km走行可能 a02 折りたたみ 電動アシスト自転車 20インチ 自転車…view page
How to Migrate Your Certification Authority Hashing Algorithm From SHA-1 To SHA-2Migrating your Certification Authority Hashing Algorithm from SHA-1 to SHA-2SHA-1 is broken, time to migrate to SHA-2Cryptographic providersMigrate your certification authority from CSP to KSPReferences
view page
ペーパーポット ティッシュケース おしゃれ トイレットペーパー対応 ティッシュホルダー ティッシュカバー かわいい 丸型 ボックスティッシュ対応 Aicollection アイコレクション 日本製…view page
The SHA-1 Attack Further Emphasizes the Need for Crypto-Agility
view page
SHA-3 vs the world SHA-3 vs the world
view page
【楽天1位!5年保証】シーリングライト 照明器具 LED 調光調色 おしゃれ 電気 北欧 照明 6畳 8畳 10畳 12畳 14畳 リモコン付き LED対応 インテリア 間接照明 天井照明…view page
SHA-3 vs the world SHA-3 vs the world
view page
Secure Hash Algorithm Secure Hash Algorithm
view page
Back to Basics: Secure Hash Algorithms
view page
期間値引クーポンあり ドレッサー おしゃれ 女優ミラー《自社製品》可愛い デスク 欧風 鏡台 お姫系 ベロア調 テーブル 幅80cm 幅60cm 幅100cm チェスト スツール LEDミラー…view page
New SHA-3 hashing IP from Barco Silex helps customers implement future-proof security
view page
amosnier/sha-2Name already in usesha-2
view page
【納期お問合せ下さい】 UNISON ガーデンシンク バル 立水栓 バルスタンド トールポット 上下蛇口 セット BARU 水栓柱 ユニソン 補助蛇口 ホース用 2口 ガーデンポット サテン…view page
What is the Difference Between SHA1 and SHA256
view page
【P5倍12/25 13-15時&最大1万円クーポン12/19-25】 応接セット 4点セット 4人 応接 ソファ 椅子 応接テーブル ソファセット 応接室 おしゃれ モダン 会議セット…view page
BACs SHA-2 – don’t make your payroll a dogs dinner
view page
¿Qué es el SHA-2 y en qué nos afecta la inminente transición desde SHA-1?
view page
お歳暮 お年賀 お菓子 ギフト スイーツ クッキー 詰め合わせ 御歳暮 冬ギフト 高級 おしゃれ 誕生日プレゼント 個包装 がらんの小石 30個入 お取り寄せスイーツ プチギフト 焼き菓子…view page
Generate SHA1 Hash from Multiple Files in Folder
view page
【5年保証】シーリングライト LED 三色切替 6灯 8灯 6畳 8畳 10畳 12畳 北欧 E26 リビング 照明 おしゃれ 回転可能 スポットライト 天井照明 照明器具 電気 寝室 食卓 洋風…view page
ACTUS カタログギフト<SHINRIN(森林)> 内祝い 結婚祝い 結婚内祝い 出産祝い 引き出物 カタログ ギフト グルメ おしゃれ 結婚 内祝 引出物 引越し祝い 引っ越し 新築祝い…view page
SHA-1 algorithm officially dead, Secure Chat not compromised
view page