Similar to クリーンネットワーク計画

Google Authenticator
Google Authenticator
I-PIN
I-PIN
ISO/IEC JTC 1/SC 27
ISO/IEC JTC 1/SC 27
Jamf
Jamf
Kon-Boot
Kon-Boot
Metasploit
Metasploit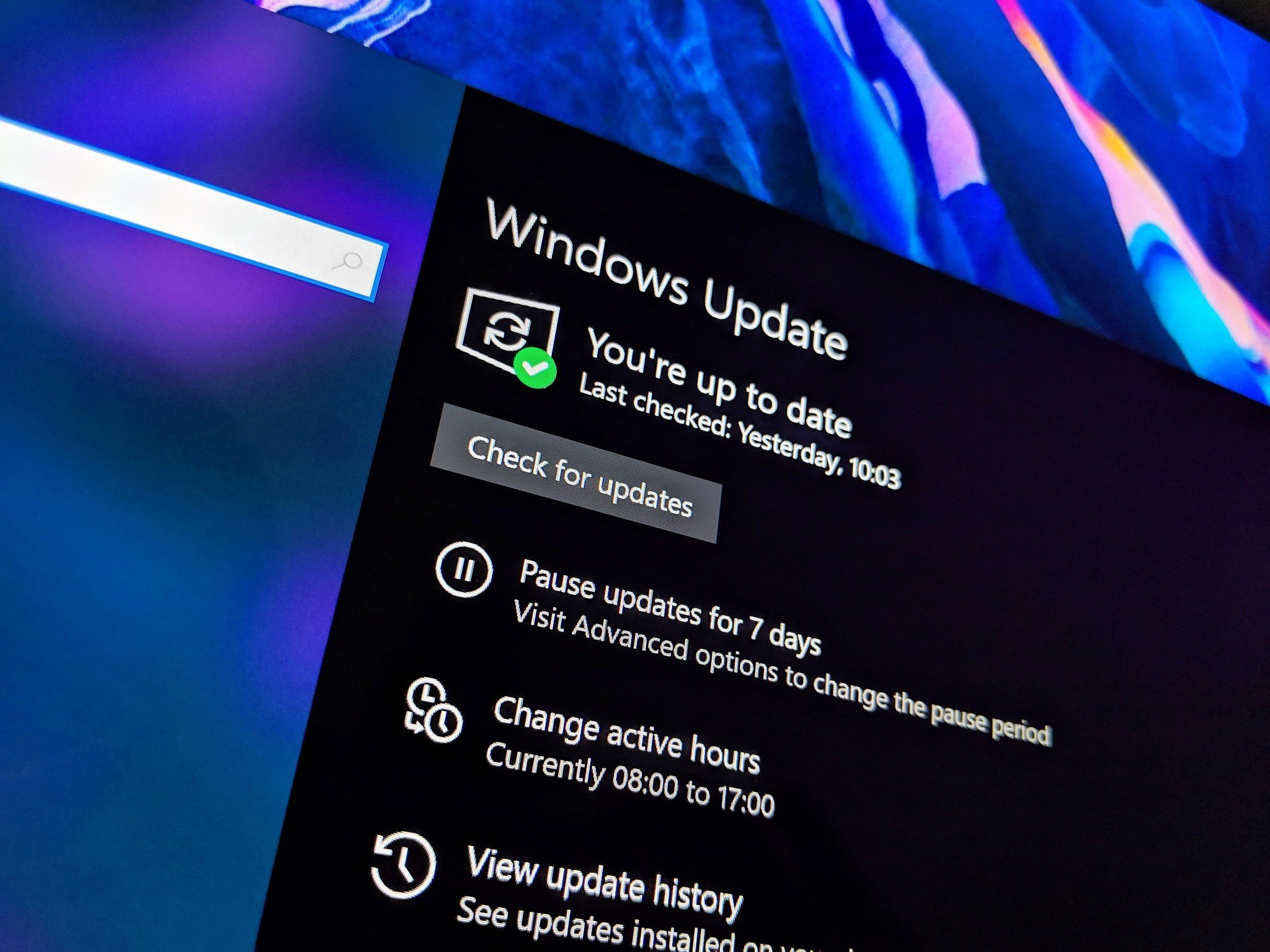
Microsoft Update
Windows Update
Microsoft Update カタログ
Microsoft Update Catalog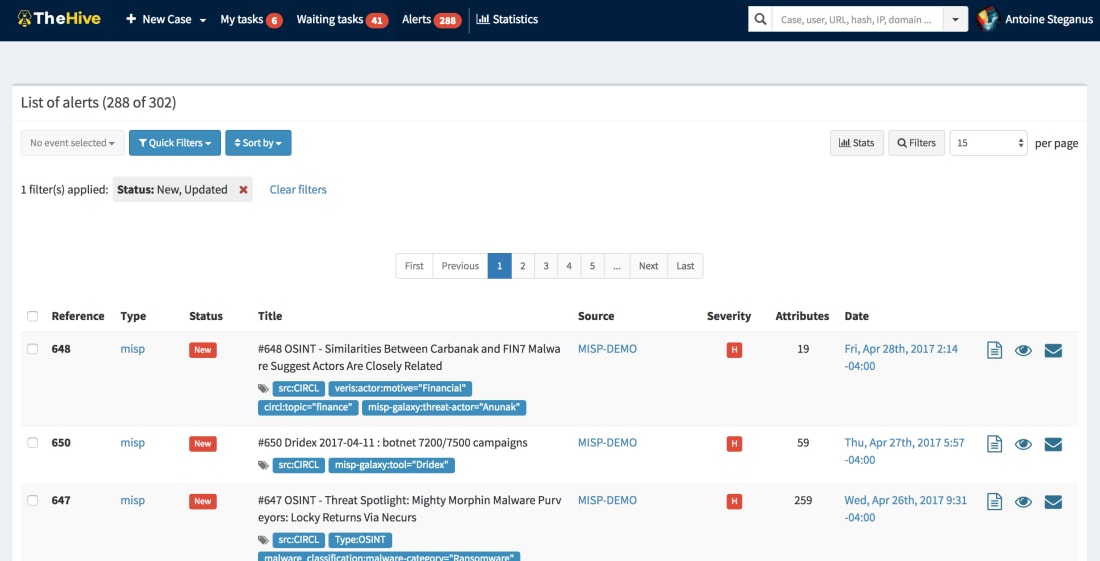
MISP
MISP Threat Sharing
NXビット
NX bit
Pika Zip
Quad9
Quad9
SecBoK

Secure computing mode
Seccomp
SecuRec

Security Content Automation Protocol
Security Content Automation Protocol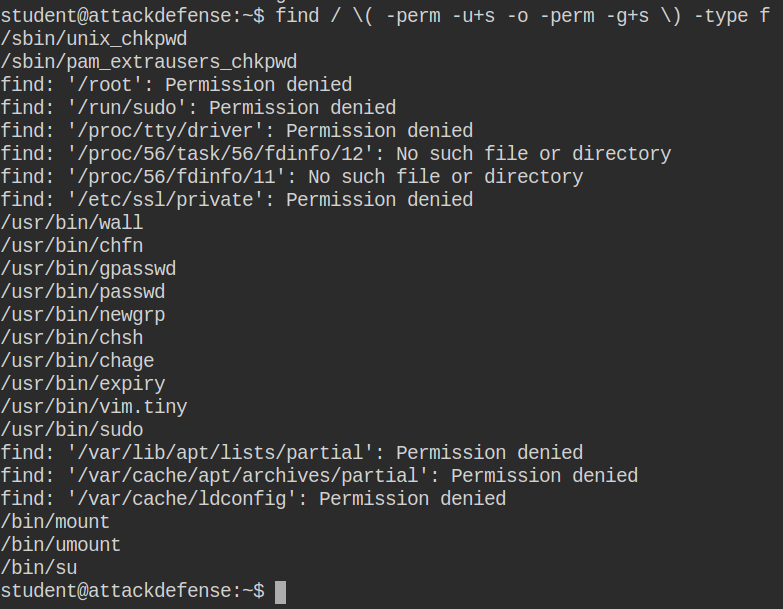
Setuid
Setuid
Spectre
Spectre (security vulnerability)
Structured threat information expression

Traffic Light Protocol
Traffic Light Protocol
Trusted Platform Module
Trusted Platform Module
USB Killer
USB killer
User and Entity Behavior Analytics
User behavior analytics悪意あるメイド攻撃
Evil maid attack
アクティブディフェンス
Active defense
ASEAN-CBP

アドレス空間配置のランダム化
Address space layout randomization
エディ・ウィレムス
Eddy Willems
