Similar to コンピュータセキュリティ

アナーキストクックブック
The Anarchist Cookbook
AAA プロトコル
Authentication, authorization, and accounting
ASEAN-CBP
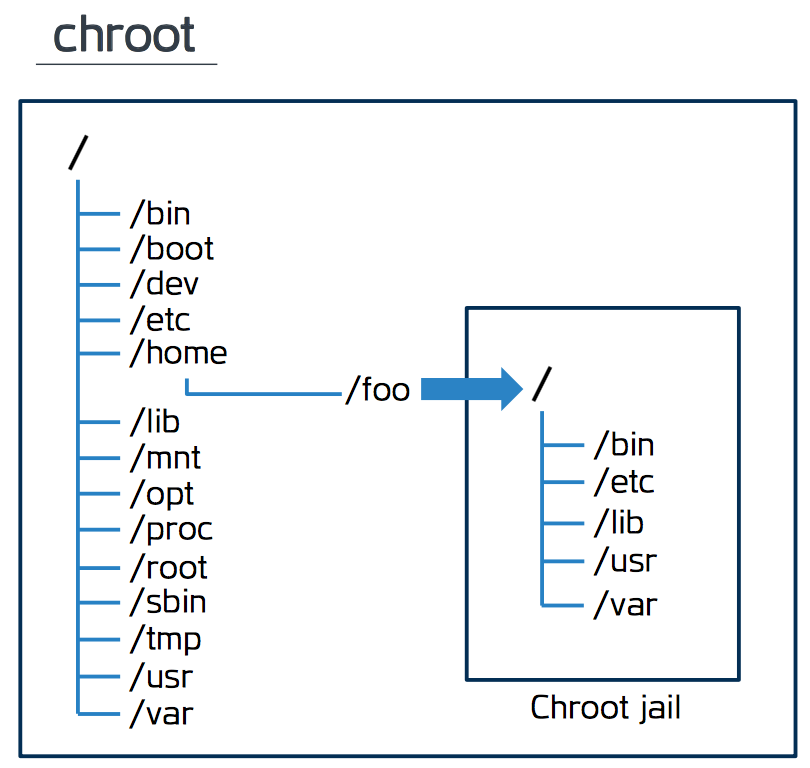
Chroot
Chroot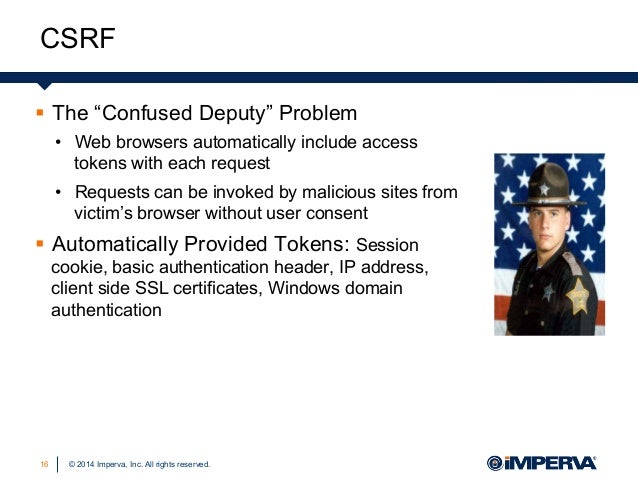
Confused deputy problem
Confused deputy problem
CPUモード
CPU modes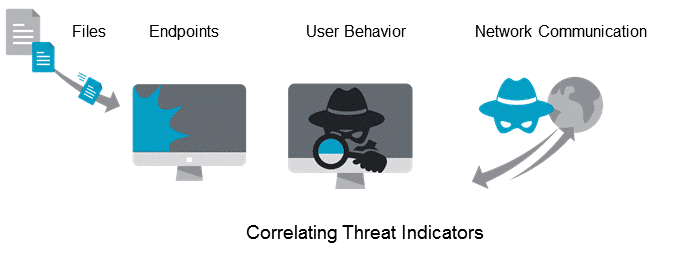
Endpoint Detection and Response
Endpoint detection and response
Enhanced Mitigation Experience Toolkit
Enhanced Mitigation Experience Toolkit
Google Authenticator
Google Authenticator
I-PIN
I-PIN
ISO/IEC JTC 1/SC 27
ISO/IEC JTC 1/SC 27
Jamf
Jamf
Kon-Boot
Kon-Boot
Metasploit
Metasploit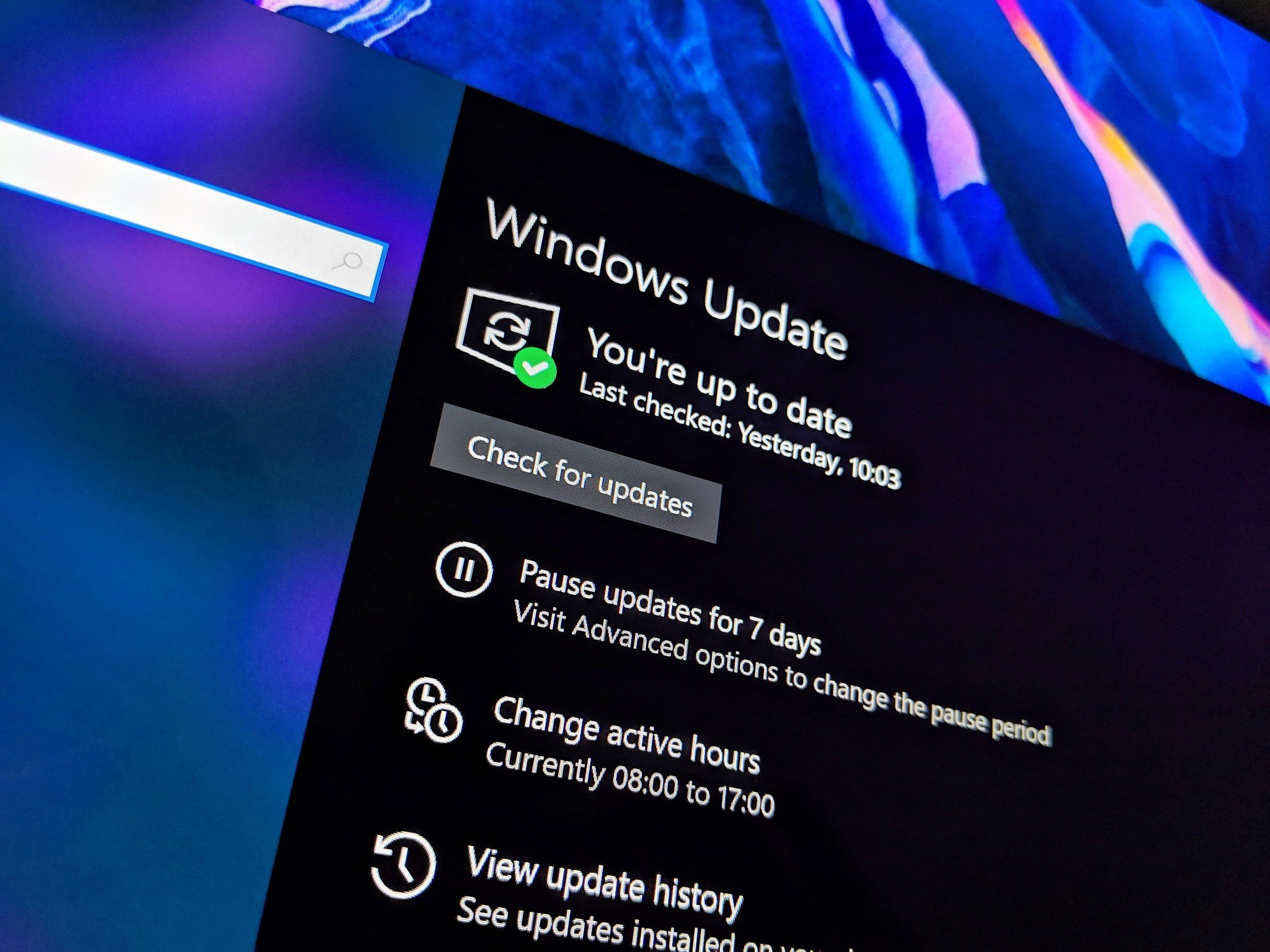
Microsoft Update
Windows Update
Microsoft Update カタログ
Microsoft Update Catalog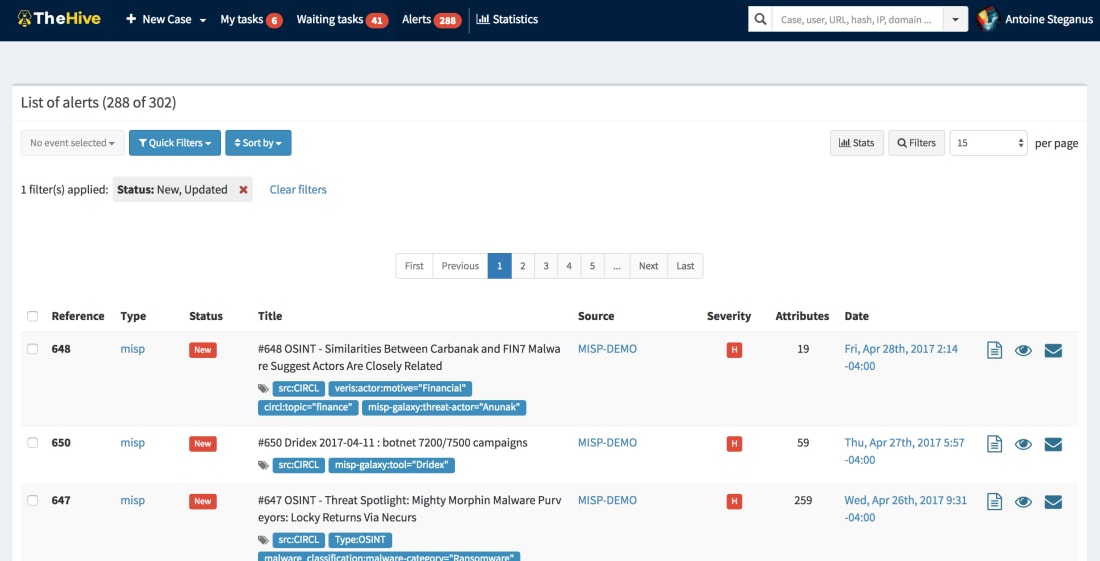
MISP
MISP Threat Sharing
NXビット
NX bit
Pika Zip

SecBoK

Secure computing mode
Seccomp
SecuRec

Security Content Automation Protocol
Security Content Automation Protocol
Setuid
Setuid
Spectre
Spectre (security vulnerability)
Structured threat information expression

Traffic Light Protocol
Traffic Light Protocol
Trusted Platform Module
Trusted Platform Module